Ads block
IoT Security Fortification: Enhancing Cyber Threat Detection Through Feature Selection and Advanced Machine Learning
Title: IoT Security Fortification: Enhancing Cyber Threat Detection Through Feature Selection and Advanced Machine Learning Conference: 2024 1st International…
Read more »
Interpretable Machine Learning for IoT Security: Feature Selection and Explainability in Botnet Intrusion Detection using Extra Trees Classifier
Title: Interpretable Machine Learning for IoT Security: Feature Selection and Explainability in Botnet Intrusion Detection using Extra Trees Classifier Confer…
Read more »
Engineering education beckons better future
Newspaper Article: Engineering education beckons better future Link: https://www.observerbd.com/news/502013 #engineeringEducation #alamgirHossain
Read more »
From Labs to Leadership – Engineering a Better Future
Article published in Business Mirror Title " From Labs to Leadership – Engineering a Better Future" Link: https://bmirror.net/from-labs-to-leadersh…
Read more »
Deep learning and ensemble methods for anomaly detection in ICS security
📚✨ Latest research paper, titled "Deep learning and ensemble methods for anomaly detection in ICS security," has just been published in the esteeme…
Read more »
Example of hierarchical data representing a library system with sections, book categories, and books in JSON and XML formats
By
Alamgir Hossain
JSON
·
XML
Provide an example of hierarchical data representing a library system with sections, book categories, and books in JSON and XML formats. Requirements: In y…
Read more »
Enhancing EDoS attack detection in cloud computing through a data-driven approach
Title: I-MPaFS: enhancing EDoS attack detection in cloud computing through a data-driven approach Journal: Journal of Cloud Computing Quartile: Q1 Impact Fac…
Read more »
Publication on security titled "Towards Superior Android Ransomware Detection: An Ensemble Machine Learning Perspective"
Publication title: " Towards Superior Android Ransomware Detection: An Ensemble Machine Learning Perspective". Journal: Cyber Security and Applicat…
Read more »
Find the Top Cited Researcher of your University through Google Scholar
Find the Top Cited Researcher of your University through Google Scholar. # UniversityResearchers hashtag # GoogleScholar hashtag # TopResearchers
Read more »
Internet of things enabled E-learning system for academic achievement among university students
Newly Published Paper: "Internet of things enabled E-learning system for academic achievement among university students". Journal: E-Learning and …
Read more »
Implication of Different Data Split Ratios on the Performance of Models in Price Prediction of Used Vehicles Using Regression Analysis
Publication of "Implication of Different Data Split Ratios on the Performance of Models in Price Prediction of Used Vehicles Using Regression Analysis&quo…
Read more »
Digital Guardians: Securing Social Media, Md. Alamgir Hossain
Digital Guardians: Securing Social Media Social media has woven itself into the fabric of our daily lives, connecting us with friends and family, keeping us …
Read more »
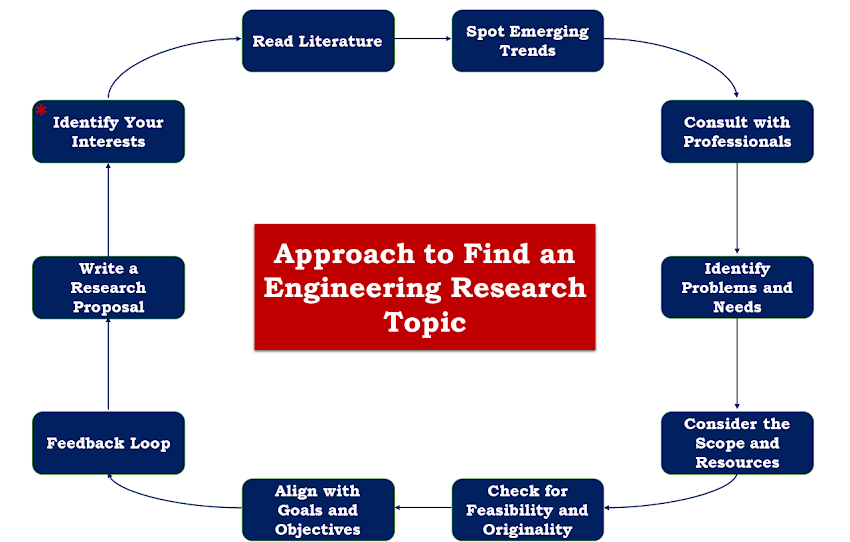
Way to Find an Engineering Research Topic
Way to Find an Engineering Research Topic Finding a compelling research topic in engineering requires a blend of curiosity, strategic thinking, and awareness…
Read more »
6G Wireless Communication Networks: Challenges and Potential Solution
6G Wireless Communication Networks: Challenges and Potential Solutions Article Title: 6G Wireless Communication Networks: Challenges and Potential Solutions J…
Read more »
Common security attacks in networks
By
Alamgir Hossain
Security
·
Tutorial
·
Writings
Here are some common security attacks in networks: 1. Denial of Service (DoS) Attack: What it is: A DoS attack aims to make a network resource or service un…
Read more »
Click any Bellow Tabs/Tags
Alamgir-Hossain
(14)
Algorithms
(5)
Android problem
(2)
ANN
(1)
ArticleWriting
(26)
Artificial Intelligence
(1)
Assembly
(1)
Bangla Love Poem
(3)
Bangla Poem
(2)
best programming solution
(9)
Books
(2)
BUET IICT MSC Admission
-2021
(1)
C
(49)
Campus
(7)
CPP
(88)
Database
(4)
Differences
(2)
Fishing
(1)
HSC
(1)
Html
(4)
interesting programming solution
(9)
Interview
(2)
It job preparation
(7)
JAVA
(97)
JavaScript
(5)
JSON
(1)
lead generation
(1)
machine learning
(8)
ML Projects
(10)
NewsPaper
(22)
Others
(13)
Perl
(23)
Php
(4)
Poem
(4)
Presentation
(1)
ProblemSolving
(3)
Project
(21)
project proposal
(2)
Prolog
(13)
Python
(33)
research
(37)
Research Tool
(1)
Security
(3)
Social Engineering
(1)
Testimonials
(5)
Tutorial
(2)
Writings
(15)
XML
(1)
YoutubeSEO
(1)
উক্তি
(1)
কবিতা-আলগীর হোসেন
(2)
রম্য
(1)
লেখনী
(36)
LATEST
3-latest-65px
Popular Posts
-
All instructions for connection & insert data in mysql from java JSP and Servlet using tomcat serverFrom this tutorial you can learn about... All instructions for connection & insert data in mysql from java JSP and Servlet using tomc...
-
% Prolog program for addition and multplication-------- % Alamgir Hossain % CSE, JUST go :- write ( 'Enter first number : ' ...
-
Inverse Lagrange’s Interpolation Formula Theory : . Example : 1. Use Lagrange’s inverse interpolation fo...
-
Project Name : Online examination system. Framework : MVC framework in java(3 layer architecture). Language: JAVA JSP, SERVLET, JS...
-
Here is the source code for online exam system using PHP, MYSQL,AJAX, JAVASCRIPT etc.... Source code for Online Exam System